Public key cryptography, also known as asymmetric cryptography, is a form of cryptography in which a user has a pair of cryptographic keys – a public key and a private key. The private key is kept secret, while the public key may be widely distributed. The keys are related mathematically, but the private key cannot be practically derived from the public key. A message encrypted with the public key can only be decrypted with the corresponding private key.
Conversely, Secret key cryptography, also known as symmetric cryptography uses a single secret key for both encryption and decryption.
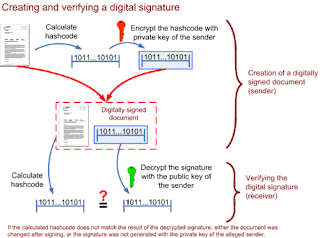
Digital Signature:
A digital signature certifies and timestamps a document. If the document is subsequently modified in any way, a verification of the signature will fail. When the sender sign a file using his private key, the receiver can verify the signature using the sender’s public key.
Look at this image:
The full wikipedia article is at:
http://en.wikipedia.org/wiki/Digital_Signature
Encrypting Documents:
A public and private key each have a specific role when encrypting and decrypting documents. Public key means the key will be known by all involved parties, private key will be your secret key, no one ever know it, if it is forged, you will have to revoke (generate obsolete certificate) the key and create new one.
Assume Ahmed and Samy each has his own pair, public and private key. When Ahmed want to send Samy a document, Ahmed will encrypt the file with Samy public key, Samy only can decrypt the file using his own private key. The encryption algorithm ensue the Samy’s private key is the only one can decrypt the file. This means the sender always encrypt using the receiver public key. The receiver only can decrypt using his own secret key.
By utilizing this Digital Signature and Encryption/Decryption, the sender can encrypt file with receiver public key, and sign it with his private key and send to the receiver. The receiver can verify the signature using sender public key, and then decrypt using his own private key. This ensure secure communications.
This scheme ensure secure communications but of course requires the exchange of public keys, there exist public key repository, such as https://keyserver.pgp.com/ . You can also send it by email to your friends.
Look at wikipedia article at http://en.wikipedia.org/wiki/Public-key_cryptography The article has graphs that simplifies the document encryption/decryption procedure.
Software Encryption Tool on Windows:
Download Windows version from:
http://www.gnupg.org/download/
You can use command line just the same as in Linux section with the same format, there exist also a GUI client tool that could make it easier for you, download Windows Privacy Tray from:
http://winpt.sourceforge.net/en/
These screen shots could show how it could be helpful.
Key manager allow you to manage your key-pairs.
File Manager will help you encrypt, decrypt files and many other functions, you can also drag and drop files.
Software Encryption Tool on Linux:
Download Linux version from
http://www.gnupg.org/download/
List Current Keys: (dollar sign mark the shell you are using)
$ gpg –list-keys
Generate New Key-pair:
$ gpg –gen-key
Encrypting Documents:
$ gpg –output docs.zip.gpg –encrypt –recipient blake@cyb.org docs.zip
Decrypting Documents:
$ gpg –output docs.zip –decrypt docs.zip.gpg
Generate Signature: (in a separate file and in clear text)
$ gpg –detach-sign –armor file1
Verify Signature: (the public key should exist in your key ring, if not, you to import it first)
$ gpg –verify file1
Look at the “The GNU Privacy Handbook” at http://www.gnupg.org/gph/en/manual.html
Now I can backup my sensitive files without worrying that the server administrators could access my sensitive files, I can even backup it on public places without any worry, thanks to Open Source and GnuPG.
You can also send and receive encrypted and/or signed emails using Thunderbird, you have to download enigmail extension from
http://enigmail.mozdev.org/